AI-Driven Precision for Policy & Compliance Alignment
Our AI engine benchmarks your current environment against leading frameworks (CIS, NIST, ISO 27001, SOC 2, GDPR, etc.) to identify exactly where gaps exist and automatically generate tailored policies that bring you closer to compliance and certification readiness.
Compliance Offerings
Your complete compliance solution, delivered through one centralized platform.

Generic Compliance
Build your compliance foundation
Establish your security program using industry-standard frameworks including NIST, CIS, SOC 2, ISO 27001, HIPAA, GDPR, and 30+ other certifications. Our structured assessment approach identifies gaps, prioritizes risks, and creates a clear roadmap to compliance, whether you're pursuing your first certification or expanding your program.
- Support for 35+ frameworks or build custom standards
- Rapid risk assessment and gap analysis
- Framework cross-mapping for multi-certification efficiency
- Scalable foundation for continuous compliance
Continuous Compliance
Automate monitoring and maintain compliance readiness 24/7.
The generic approach is overly reliant on static checklists and manual processes that fails to account for operational needs and cyber survivability requirements. These limitations left security systems vulnerable to sophisticated adversaries and slowed the delivery of secure capabilities to the field. The continuous compliance approach addresses these gaps by shifting from "snapshot in time" assessments to dynamic, automated, and continuous risk management, enabling cyber defense at the speed of relevance required for handling modern threats.
Our Protect Lite service delivers real-time compliance monitoring without complex setup or integration. Client Trust Center will be leveraged to centralize evidence management with automated monitoring. Connects securely in read-only mode to your evidence vault and automatically verifies controls, keeping you audit ready and risk free.
- No agent or software installation required
- Real time compliance tracking
- Read only environment access
- Risk free integration
Features of continuous compliance.
Automation
Driving efficiency and scale across compliance operations
Critical Controls
Identifying and tracking the controls that matter most to cybersecurity
Continuous Monitoring
Enabling real-time situational awareness to achieve constant cybersecurity posture
Cyber Survivability
Enabling operations in contested environments
Training
Upskilling personnel to meet evolving challenges
Enterprise Services & Inheritance
Reducing duplication and compliance burdens
Operationalization
Ensuring stakeholders near real-time visibility of cybersecurity risk posture
Reciprocity
Reuse assessments across systems
Cybersecurity Assessments
Integrating threat-informed testing to validate security
Upload your evidence once. Infinite compliance wins.
Instead of collecting the same evidence for every audit, We let you upload your compliance documents once, and reuse them across every certification you need. Your compliance team’s new superpower: Reuse instead of Redo, saving you time, money, and headaches!





Every audit feels the same: the same documents, the same screenshots, the same scramble. It’s repetitive and expensive. We built a smarter way. One place, one process, one upload — and your compliance workload drops dramatically. It’s all about “ compliance without the grind. ”









Your Compliance Journey
We guide you from initial framework selection through certification and beyond, with continuous monitoring that keeps you compliant year-round.
Gap Analysis
We go beyond traditional compliance mechanisms with AI-powered gap analysis that reviews your existing cybersecurity policies, controls, and posture to recommend required evidence and suggest enhancements to existing ones.
A detailed understanding of your vulnerabilities and risk profile
Tailored policy updates aligned with NIST, CIS, and ISO standards
Actionable compliance remediation roadmap with prioritized fixes
Continuous compliance readiness and audit preparation support
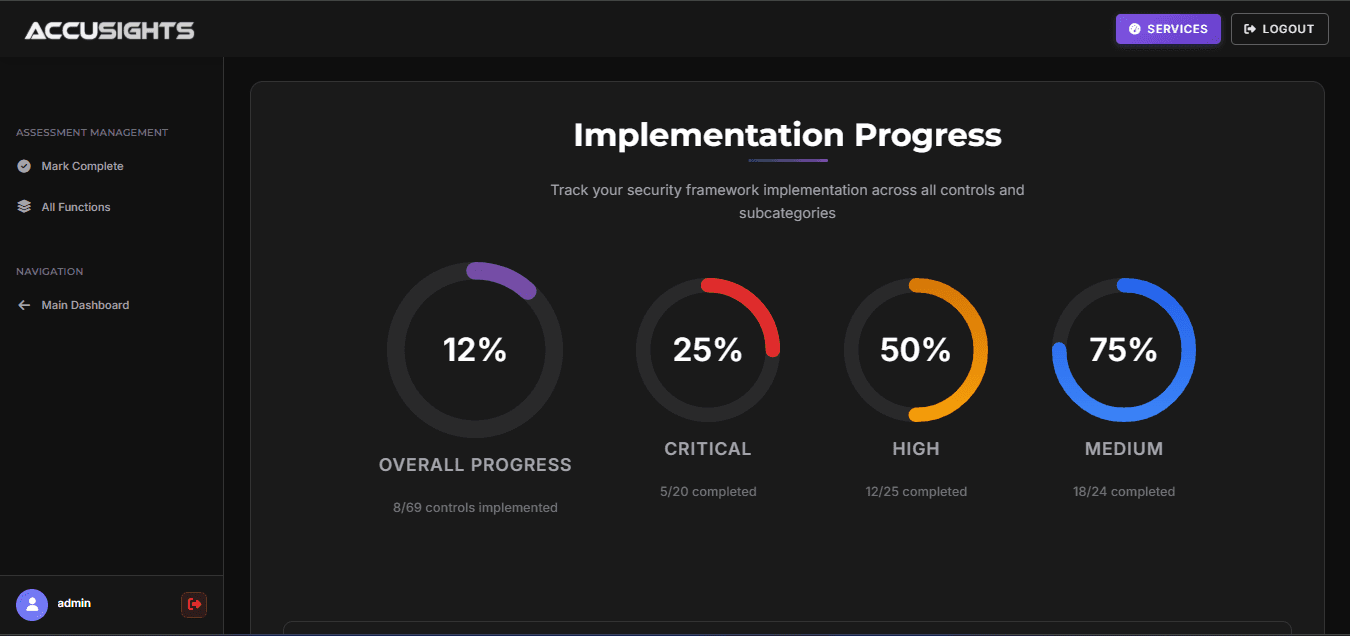
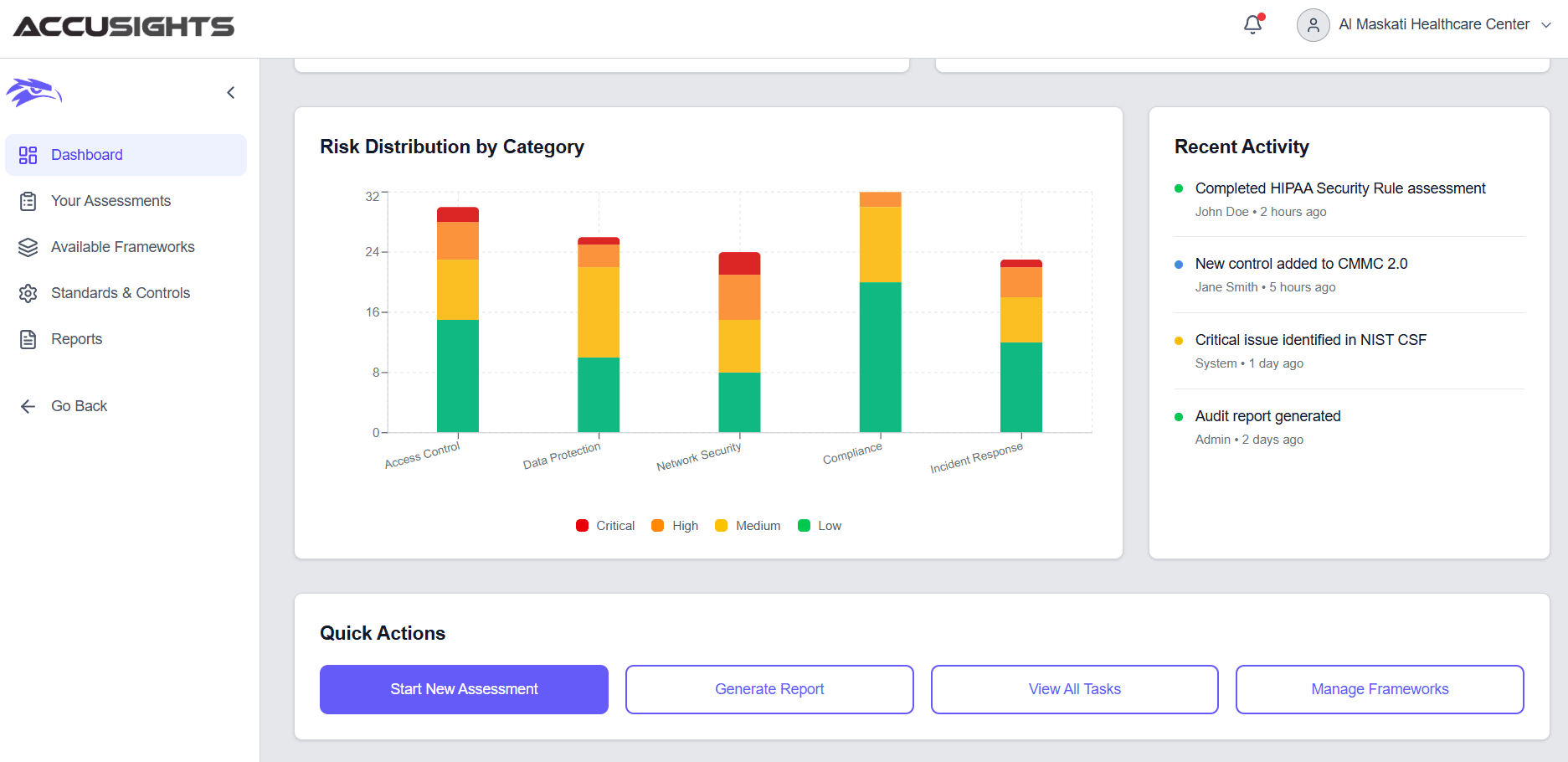
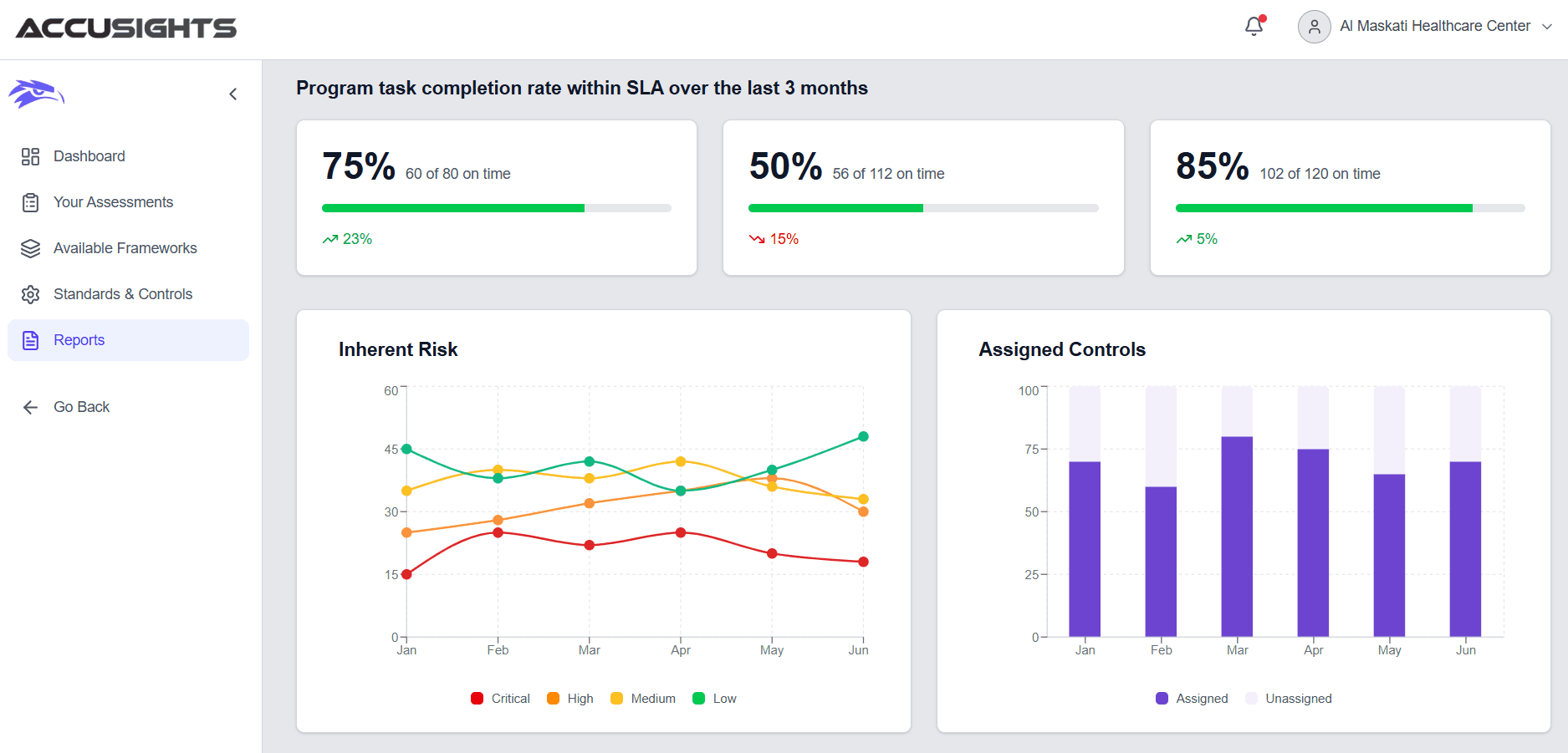
Comprehensive Assessment Dashboard
Analyze your security posture in real-time with actionable insights
Benefits of Automated
Compliance Gap Assessment
AI-powered analysis that identifies control deficiencies and accelerates framework alignment.
Comprehensive Risk Intelligence
AI-driven vulnerability assessment with precise risk scoring, control gap identification, and automated policy recommendations mapped to NIST, CIS, and ISO frameworks.
Accelerated Certification Path
Reduce time-to-compliance by up to 60%, with AI-powered prioritization, automated evidence collection, and framework-specific remediation workflows.
Continuous Compliance Monitoring
Real-time control validation with automated drift detection, regulatory change tracking, and always-on audit readiness across multiple frameworks.
Proactive Security Hardening
Reduce attack surface and compliance violations through automated threat correlation, predictive risk analytics, and continuous control effectiveness validation.
Align with Frameworks
Implementing the findings from our gap analysis, Make you aligned with target Frameworks.
Enhanced Security Posture
45% reduction
in detected vulnerabilities within the first 90 days
Continuous Compliance
80% reduction
in manual compliance tasks
Risk Mitigation
2× faster
identification of misconfigurations
Audit Readiness
260+ hours saved
per audit cycle
Brand Protection
Zero major compliance gaps
reported after onboarding
Operational Efficiency
100% control mapping
in real-time
Discover Your Compliance Gaps
Book a free AI gap scan and get a comprehensive understanding of your compliance posture across all major frameworks.